Introducing DevSecOps
In the rapidly evolving landscape of software development, security has emerged as a critical concern for organizations worldwide. Traditional approaches, where security is treated as an afterthought, no longer suffice to protect against sophisticated and ever-evolving cyber threats. In response to this challenge, DevSecOps has emerged as a groundbreaking revolution, integrating security seamlessly into the entire software development lifecycle. DevSecOps transforms the way we build software, making security an integral part of the development process from inception to deployment. In this blog post, we will delve into what DevSecOps is, why it is essential, and how it is reshaping the software development landscape.
Understanding DevSecOps: Integrating Security Throughout the Software Lifecycle
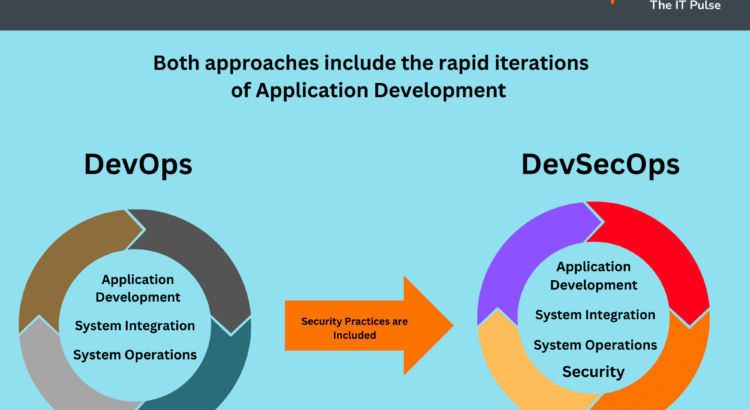
DevSecOps is an extension of the DevOps philosophy that seeks to bridge the gap between development (Dev), operations (Ops), and security (Sec) teams. Unlike traditional models, where security concerns are addressed in isolation after development, DevSecOps promotes the integration of security practices and principles into every step of the software development pipeline.
Features of a Successful DevSecOps Pipeline
With the DevSecOps methodology on the rise, tech titans and business leaders are wondering what makes an effective DevSecOps pipeline. What security elements should be integrated into an existing continuous integration, continuous delivery, and continuous deployment pipeline to ensure successful and timely delivery?
Let’s take a look at the top three features that can assist firms in developing successful DevSecOps pipelines in this blog.
1. Pre-Commit Checks are a Must!
Pre-commit checks are required to assure the DevOps pipeline’s complete security. Pre-commit checks are used to uncover security concerns before committing changes to source code repositories. They aid in the reduction of time-consuming manual chores and the increase of productivity. In addition to these checks, good DevSecOps pipelines incorporate integrated unit tests, static code analysis, and code review to aid in the discovery of flaws and bugs in code before it is committed to the repository.
2. Commit-Time Testing should be Implemented!
At each check-in to the source-code repository, the application should be tested in an automated and painless manner. It is critical to design and run tests on the application to ensure that it functions properly. These tests should run and fail quickly in order to give coders timely results. DevOps teams may empower themselves and prevent important and high-risk vulnerabilities by incorporating static application security testing (SAST) solutions like Reshift security, Brakeman, and Findbugs.
3. Deployment Checks to be Performed!
Once the build has been completed, it is time to deploy the application to a test environment and run before- and post-deployment security tests to enforce security configurations. Executing these deployment checks assures the application’s functional and operational health, assuring DevOps teams that there are no security concerns within the app. Without a doubt, relying on DevSecOps services allows for speedy and painless app deployment, relieving developers of the burden of resolving security bugs and issues, which typically consume a substantial portion of their daily productivity.
Including these DevSecOps features not only improves app security against major risks and threats but also improves deployment quality and allows organizations to capitalize on the true benefits of Microservices.
Why DevSecOps is Crucial: The Shift-Left Approach
The heart of DevSecOps lies in the “shift-left” approach to security. Instead of considering security as a final checkpoint, DevSecOps emphasizes introducing security considerations early in the development process. This proactive strategy yields several crucial benefits:
- Enhanced Resilience: By addressing security from the outset, DevSecOps builds a robust and resilient software architecture, reducing vulnerabilities and minimizing potential security risks.
- Rapid Threat Response: Integrating security practices throughout the development pipeline enables teams to quickly identify and respond to security threats and vulnerabilities.
- Continuous Security Monitoring: DevSecOps fosters a culture of continuous security monitoring, ensuring that applications remain secure even after deployment, and enabling swift remediation of emerging issues.
- Collaborative Responsibility: DevSecOps fosters collaboration and communication between development, operations, and security teams, breaking down silos, and promoting shared responsibility for security.
Key Principles and Best Practices of DevSecOps
To achieve the goals of DevSecOps effectively, organizations adopt several key principles and best practices:
- Automated Security Testing: DevSecOps leverages automated security testing tools such as Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Software Composition Analysis (SCA). These tools help identify and rectify security flaws at an early stage of development.
- Infrastructure as Code (IaC): Employing IaC principles, organizations define and version-control security configurations, ensuring consistent and secure infrastructure setups.
- Secure Code Reviews: Regular secure code reviews facilitate the identification and mitigation of security issues and vulnerabilities within the codebase.
- Continuous Security Training: Providing ongoing security training for development teams ensures they stay abreast of the latest security best practices and emerging threats.
- Security Champions: Designating security champions within development teams fosters security awareness and promotes the adoption of secure coding practices.
- Security Automation: Automation of security-related tasks reduces the manual effort required to address security concerns, allowing teams to focus on building and delivering software.
The Transformative Impact on Software Development
DevSecOps profoundly impact the software development landscape, yielding numerous advantages:
Agile and Secure Deployment: Addressing security concerns early in the development lifecycle enables organizations to deploy applications more rapidly while maintaining a strong security posture.
- Reduced Vulnerabilities: Through automated security testing and code reviews, DevSecOps minimizes vulnerabilities, reducing the attack surface for potential threats.
- Compliance: DevSecOps practices facilitate compliance with industry standards and regulations, safeguarding organizations from non-compliance penalties.
- Heightened Customer Trust: Building secure software instills confidence in customers, leading to increased trust and loyalty toward the application and the organization.
Why is it important for teams to understand the difference between DevOps and DevSecOps?
Though it may be difficult for teams to distinguish between DevOps and DevSecOps techniques, it is necessary for developing efficient DevSecOps pipelines. SRE and DevOps teams that grasp the distinction between DevOps and DevSecOps are well-equipped to make critical decisions to improve the efficiency of their app development pipelines. Furthermore, it enables them to make the necessary changes to existing processes in order to improve the speed, agility, and security of the software delivery process.
DevSecOps: Why is it the best approach to support Microservices?
By integrating these DevSecOps features in the build & deploy pipelines and procuring DevSecOps services, enterprises can prevent high risks and streamline their delivery process. DevSecOps practices help in solving the security & compliance challenges of Microservices applications and help IT folks in ensuring that the apps are being deployed in a secure and hassle-free manner.
Easy scalability, improved resilience, high reliability and many more benefits of Microservices such as these are the major reasons why businesses prefer to go for Microservices these days. But, managing them is a daunting task.
DevSecOps features are offered by Spundan
Most business organizations today are migrating to Microservices architecture for leveraging the benefits of Microservices. But, with modularity comes the huge pain of managing these complex life cycles of Microservices. Building and creating security features in applications only adds to the complexity of these Microservices challenges. Choosing the right Microservices Architecture, Tools, and Platforms can help overcome the intricacies of Microservices challenges. Spundan is an End to End DevOps & DevSecOps solution provider.
At @spundan, our strength lies in the powerful expertise and extensive experience of our team. We excel in implementing DevOps, DevSecOps, and following robust methodologies and processes.
Visit our DevOps portal here: https://devops.spundan.com
Conclusion: Embracing a Secure and Agile Future
In conclusion, DevSecOps represents a transformative shift in software development, empowering organizations to proactively address security challenges in the dynamic digital landscape. By seamlessly integrating security into every facet of the development pipeline, DevSecOps establishes a solid foundation for creating secure, resilient, and dependable software applications. Moreover, it fosters a collaborative environment where development, operations, and security teams work hand in hand, upholding the highest standards of security.
As technology continues to evolve, DevSecOps remains at the forefront, driving innovation and enabling organizations to stay ahead of security threats while confidently delivering cutting-edge software solutions. Embracing DevSecOps paves the way forward toward a future where security and agility harmonize, making it an indispensable approach for modern software development.
Implementing DevSecOps practices and leveraging DevSecOps services empowers businesses to conduct comprehensive assessments of system access and information availability. By utilizing DevSecOps methods, enterprises can strategically limit and restrict access to confidential data, bolstering defenses against security risks and cyber breaches, and elevating overall security measures. This comprehensive approach to security fortification is essential in today’s digital landscape, ensuring businesses can thrive with confidence while safeguarding their valuable assets and data.